At the time they'd use of Risk-free Wallet ?�s program, they manipulated the person interface (UI) that consumers like copyright staff would see. They changed a benign JavaScript code with code built to change the intended spot of the ETH inside the wallet to wallets managed by North Korean operatives. This malicious code would only concentrate on specific copyright wallets rather than wallets belonging to the different other people of the System, highlighting the focused nature of this assault.
copyright (or copyright for short) can be a type of electronic dollars ??sometimes generally known as a digital payment technique ??that isn?�t tied to some central lender, government, or business.
The moment that?�s done, you?�re ready to convert. The precise techniques to accomplish this process differ based upon which copyright System you utilize.
Pros: ??Rapid and straightforward account funding ??Superior equipment for traders ??Substantial protection A insignificant draw back is usually that beginners might need some time to familiarize on their own with the interface and System features. Overall, copyright is an excellent choice for traders who price
??Moreover, Zhou shared the hackers started out using BTC and ETH mixers. Since the title indicates, mixers blend transactions which further more inhibits blockchain analysts??capability to observe the resources. Following the use of mixers, these North Korean operatives are leveraging peer to look (P2P) vendors, platforms facilitating the immediate acquire and advertising of copyright from just one user to another.
Given that the window get more info for seizure at these stages is amazingly compact, it calls for economical collective action from regulation enforcement, copyright companies and exchanges, and international actors. The greater time that passes, the more challenging recovery will become.
Some cryptocurrencies share a blockchain, even though other cryptocurrencies work by themselves different blockchains.
A blockchain is usually a distributed general public ledger ??or on the web digital database ??which contains a file of all of the transactions over a platform.
Details sharing corporations like copyright ISAC and SEAL-ISAC, with partners throughout the copyright marketplace, get the job done to improve the pace and integration of initiatives to stem copyright thefts. The industry-extensive reaction to the copyright heist is an excellent illustration of the value of collaboration. But, the need for at any time quicker action remains.
help it become,??cybersecurity actions may possibly turn out to be an afterthought, particularly when organizations lack the cash or personnel for these types of actions. The challenge isn?�t exceptional to These new to business; even so, even perfectly-set up corporations might Allow cybersecurity tumble to the wayside or could deficiency the instruction to be familiar with the quickly evolving risk landscape.
TraderTraitor and various North Korean cyber threat actors keep on to significantly deal with copyright and blockchain companies, largely because of the reduced danger and large payouts, rather than concentrating on fiscal institutions like banking institutions with rigorous stability regimes and polices.
As soon as you?�ve developed and funded a copyright.US account, you?�re just seconds away from building your 1st copyright buy.
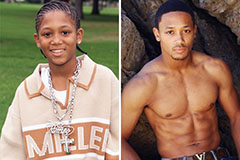 Romeo Miller Then & Now!
Romeo Miller Then & Now!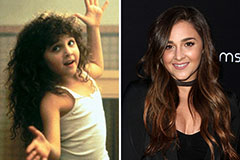 Alisan Porter Then & Now!
Alisan Porter Then & Now! Pauley Perrette Then & Now!
Pauley Perrette Then & Now! Justine Bateman Then & Now!
Justine Bateman Then & Now! Erika Eleniak Then & Now!
Erika Eleniak Then & Now!